SSH Mastery: Essential Commands & Troubleshooting Tips [2024]
Ever felt lost navigating the intricate pathways of your Linux server or VPS? Mastering SSH commands is no longer optional; its the cornerstone of effective server management. Without it, managing your web presence becomes an uphill battle.
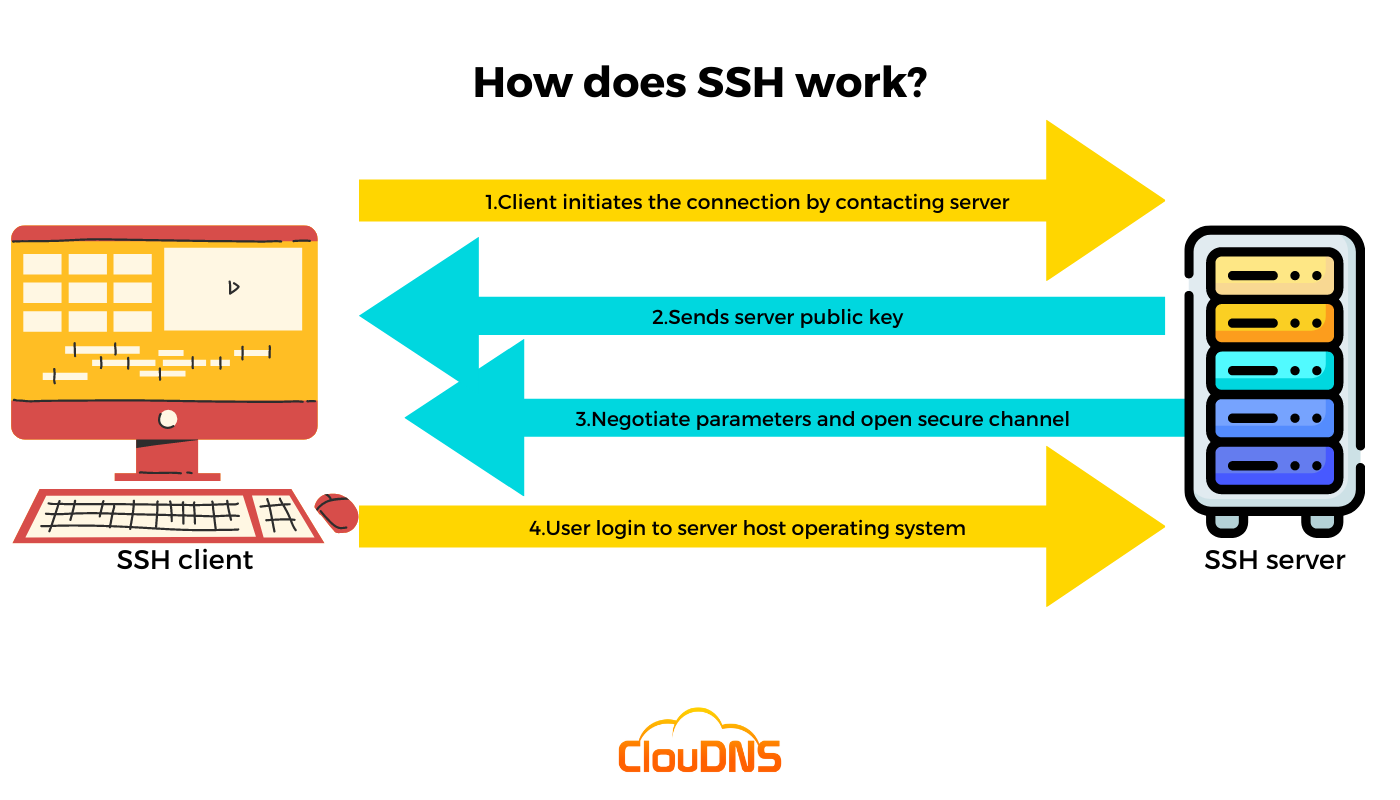
Secure Shell (SSH) is the bedrock of secure remote access. Its the encrypted tunnel that allows you to manage your servers, transfer files, and execute commands from anywhere in the world. It's the linchpin for webmasters and system administrators. Forget clunky interfaces and insecure protocols; SSH is your streamlined solution.
| Category | Details |
| Name | Secure Shell (SSH) |
| Description | A cryptographic network protocol for secure remote access and command execution. |
| Function | Enables users to securely access and manage remote servers over an encrypted connection. |
| Key Features |
|
| Primary Use Cases |
|
| Benefits |
|
| Drawbacks |
|
| Alternatives |
|
| Further Reading | SSH.com |
The beauty of SSH lies in its simplicity. The basic command to log into a remote machine is straightforward. To connect to a remote computer named 'sample.ssh.com', you simply type ssh user@sample.ssh.com at your shell prompt. This command initiates a secure connection to the specified server, allowing you to interact with it as if you were sitting right in front of it.
- Unveiling Filmy4wap South Movie 2022 Your Ultimate Guide
- Filmyfly One South Your Ultimate Entertainment Hub
However, the first time you connect to a remote machine using SSH, you might encounter a security prompt. A message will appear, stating: "The authenticity of host 'sample.ssh.com' cannot be established." This is a security measure to ensure you're connecting to the correct server and not falling victim to a man-in-the-middle attack. You'll be asked to verify the host's fingerprint. Once verified, SSH stores the host's key in your ~/.ssh/known_hosts file, preventing future warnings unless the host key changes.
SSH offers a range of options to customize your connection. You can specify a port number using the -p flag, like so: ssh -p 2222 user@sample.ssh.com. This is particularly useful if the server is configured to listen on a non-standard port. For enhanced security, you can use a private key file for authentication. The command ssh -i ~/.ssh/id_rsa user@sample.ssh.com instructs SSH to use the specified private key file for authentication, eliminating the need to enter your password each time.
Debugging connection issues can be frustrating, but SSH provides a valuable tool: verbose mode. By using the -v flag, you enable verbose output, which echoes everything SSH is doing while establishing the connection. This is immensely helpful in pinpointing the source of connection failures. For instance, ssh -v user@sample.ssh.com will display a detailed log of the connection process, revealing any errors or warnings that might be hindering your connection.
- Aditi Mistry Latest Updates Videos And News You Must See
- Hdhub4u In Hollywood Your Ultimate Guide To The World Of Movies And Entertainment
For those managing numerous servers, learning a set of essential SSH commands is paramount. These commands allow you to navigate your system, modify files and folders, and perform a wide range of administrative tasks with ease. Thankfully, mastering these commands is within reach. A well-curated list of 17 essential SSH commands can equip any webmaster with the necessary tools to manage their servers effectively.
One of the cornerstones of secure SSH access is key-based authentication. After generating an SSH key pair, you need to copy the public key to the remote server. This allows you to log in without entering your password. The ssh-copy-id command simplifies this process. To copy the public key to a remote server, you would enter the following command on the client machine: ssh-copy-id user@sample.ssh.com. This command automates the process of adding your public key to the ~/.ssh/authorized_keys file on the remote server.
Occasionally, you might encounter a warning when copying your SSH key to a remote server, indicating that the IP address or hostname already exists in your ~/.ssh/known_hosts file. This can happen if the server's key has changed, or if you've previously connected to a different server with the same IP address. To resolve this, you need to remove the existing entry from the ~/.ssh/known_hosts file. This can be achieved using the ssh-keygen -R hostname command. For example, ssh-keygen -R sample.ssh.com will remove the entry for 'sample.ssh.com' from your known_hosts file.
The world of Internet of Things (IoT) brings new challenges and opportunities for secure remote access. Preparing to SSH into an IoT device requires a few essential steps. Before you can establish a secure connection, you need to ensure that SSH is enabled on your device. Some IoT devices may have SSH disabled by default for security reasons. You'll need to consult your device's documentation to determine how to enable SSH. This usually involves accessing the device's configuration interface, either through a web browser or a command-line interface.
The first step in preparing an IoT device for SSH access is to ensure that SSH is enabled. Many IoT devices, for security reasons, come with SSH disabled by default. Enabling SSH typically involves accessing the device's administrative interface, which may be a web-based GUI or a command-line interface. The specific steps will vary depending on the device manufacturer and model. Consult your device's documentation for detailed instructions.
When logging in remotely with SSH, you can configure your local settings to be forwarded. This allows you to access resources on your local machine from the remote server. However, not all SSH servers support this feature. For example, as of November 2010, CSC's Solaris SSH server did not permit forwarding of environment variables, which is necessary for this to work. This limitation can affect your ability to use certain applications or scripts that rely on specific environment variables.
In essence, SSH is a versatile and indispensable tool for anyone managing remote systems. From basic server administration to secure file transfers and IoT device management, SSH provides a secure and efficient way to interact with remote machines. Mastering SSH commands and understanding its various options and configurations is a worthwhile investment for any webmaster, system administrator, or IoT enthusiast.
To connect to a remote system using SSH, we will use the SSH command. The most basic form of the command is:
First of all, press [option]+[u] simultaneously. without pressing any other key, press the letter to be accented with the umlaut mark.
For example, to type (umlaut u) on mac, press [option] + [u] as the first step.
Then without pressing any other key or pressing the mouse, type the letter u.
These are some simple multiple choice questions (MCQs) on the topic of Internet of Things (IoT) with the correct solution with it.
You can have a look through it just to check/verify your theory knowledge in IoT domain.
Secure Shell (SSH) offers a range of benefits when it comes to implementing secure communication in IoT deployments.
Lets explore some of the key advantages of using SSH in IoT.
One of the primary benefits of SSH is its ability to encrypt data exchanged between devices
- Unveiling The Truth Behind Subhashree Sahus Viral Mms Video
- Movierulz Kannada Movies Latest Releases News 20242025 Your Ultimate Guide

SSH Tutorial What is SSH, Encryptions and Ports
What is SSH? ClouDNS Blog

What is a Secure Shell Protocol (SSH)? Everything to Know